Assuming you want to create a new record in an existing Access database table named “tbl_user” with fields “user_id”, “user_cat”, and “psw”, the following VBA code should do the trick: Sub CreateUser() ' Open a connection to the Access database Dim db As DAO.Database Set db = CurrentDb() ' Create a new record in the tbl_user table Dim rs ...
Read More »Author Archives: Edmund Aikore
ChatGPT: The AI-Powered Tool Changing the Game for Businesses
ChatGPT is a variant of the GPT (Generative Pre-trained Transformer) model developed by OpenAI, which is a state-of-the-art language model that uses deep learning techniques to generate natural-sounding text. The model is trained on a massive dataset of text, allowing it to learn patterns and structures in human language. What is ChatGPT Made for? One of the key features of ...
Read More »Instagram can now check your age with your face with new AI innovation
New AI Tech on instagram to verify your age. Other method available to verify your true age in the Yoti technology is keeps evolving in the Machine Learning process.
Read More »What Really is The Difference Between JPEG And JPG
You really would see these different in Windows, but in this article you discover why JPEG is the same as JPG
Read More »How to Move Archived Mail from a PST File to Office 365
Summary: When it comes to moving archived PST email to Office 365, you can choose to import the files with a few steps. However, migration may not be smooth when importing large-sized PST files to an Office 365 account. While most of the migration process may fare well, there’s a possibility that some of your email data might become corrupt ...
Read More »Download Microsoft Outlook
Hey, thank you for visiting this page just as Microsoft outlook one important and most used application on the web and mobile devices for managing your email box and for contacts you can read more about Microsoft outlook here Android version can be downloaded from Playstore using this link here PC and other version can be downloaded from here
Read More »Best Email Client Application for all Platforms
Read about the Best Email Client Application for all Platforms accross all devices.
Read More »How to Extract, Copy Text from Any Dialog Box
Sometimes when working on your PC you might experience some dialogue boxes popping up, error messages and you want to actually send it or put down the text displayed on the dialogue box. The easiest method majority of computer users use is by typing the text displayed on the dialog box. This can be tedious at times especially when the ...
Read More »What is a Virus?
A computer virus is a program that replicates itself by copying itself to another program. In other words, computer virus replicates or spreads by copying itself into other executable programs or documents. Computer virus is created to first infect then get access and control a computer to steal user important data. Viruses are designed by hackers with a venomous intent ...
Read More »A problem occurred while Microsoft Access was communicating with the OLE server or ActiveX Control
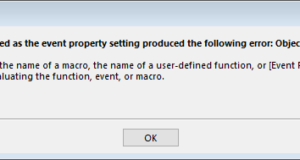
If you are using Microsoft access and you get an error such as the picture below you know that the source code in your form can never run. You must have discovered that other forms have their codes running but a particular form keeps giving you errors. One critical error I discovered recently while developing a database using Microsoft Access ...
Read More »